Atlas Systems Named a Representative Vendor in 2025 Gartner® Market Guide for TPRM Technology Solutions → Read More

Cyber Incident Response: Your Guide to Effective Recovery


15 min read | Last Updated: 02 Dec, 2025
TL;DR
- Six-phase process critical: Preparation, identification, containment, eradication, recovery, and incident review guide teams through systematic response minimizing damage and speeding recovery
- Clear roles prevent chaos: Incident manager leads overall response, tech lead diagnoses issues, communications manager handles messaging, subject matter experts provide specialized knowledge
- Three top frameworks recommended: NIST SP 800-61, SANS Institute Incident Response Process, and ISO/IEC 27035 provide structured approaches for detection and recovery
- Atlas 24/7 MDR services: Managed detection and response continuously monitors systems using AI-based threat intelligence, conducts vulnerability scans, provides cloud security protection
In May 2020, Blackbaud, a third-party vendor for Trinity Health responsible for backing up its donor database, faced a major test when a ransomware attack hit.
Although the hackers managed to steal a small portion of data linked to Trinity Health, Blackbaud’s quick thinking and well-honed IT cyber security incident response plan helped block the attack before it could cause further damage.
This event highlights the critical importance of an organization's robust incident response plan. Now that you understand the importance of being prepared, let's explore the steps to build a strong cyber incident response strategy.
What Is A Cyber Incident Response?
A cyber incident response plan is a prepared plan designed to quickly contain the damage and help you recover as fast as possible. Let’s say a business suddenly faces a cyberattack. Customer trust, brand reputation, and critical data are all on the line.
That’s where a cyber incident response comes into play. When an incident occurs, your team uses the plan to determine exactly how the attacker got in, what actions they took, and whether any sensitive information was compromised.
This process strengthens your overall security and gives you the information you need to address any legal or regulatory issues that might arise.
Why is Cyber Incident Response Important?
Cyberattacks are frequent today, getting bigger and smarter every day. When an incident strikes, having a robust response plan helps ensure you’re not caught off guard.
The experts swiftly assess which systems are hit, isolate and fix problems, and the hospital’s Incident Management Team (IMT) keeps everything stable and ensures patient care is not compromised. In short, a solid cyber incident response plan minimizes damage and speeds up recovery, protecting your organization’s data, reputation, and, most importantly, the people who depend on your services.
By the way, it's worth mentioning that the U.S. Healthcare and Public Health Sector Coordinating Council (HSCC) recently released the Medical Product Manufacturer Cyber Incident Response Playbook (MPM CIRP).
This playbook is a detailed guide that offers step-by-step recommendations and processes specifically designed for medical product manufacturers to handle cyber incidents.
Importance Of Recovery In The Incident Management Lifecycle
Recovery is the heart of incident response. It’s what gets your organization back on track after a breach. It means restoring your critical systems and data quickly, ensuring you can resume operations and serve customers without interruptions.
Essentially, recovery helps minimize the impact of an incident so that you can bounce back stronger and better prepared for the future.
During recovery, you might begin by testing your backups in a secure, isolated environment to ensure they’re unaffected, then proceed to fully restore systems once you’re confident there’s no risk of re-infection.
You’ll also have to work with legal and PR experts to craft accurate, vetted statements for regulators, clients, and the media.
Who Is Responsible For Cyber Incident Response?
When an incident occurs, clear roles are essential. You don’t want multiple people duplicating efforts or important tasks getting overlooked because everyone assumed someone else was on it.
Here is a list of roles and responsibilities you must assign if things go haywire.
|
Role |
Primary Responsibility |
Secondary Tasks |
Also Known As |
|
Incident Manager |
Leads the overall response during an incident. |
Delegates tasks and handles any unassigned work. |
Incident Commander, Major Incident Manager |
|
Tech Lead |
Guides technical response, diagnoses issues, and implements fixes. |
Shares update and documents key actions for review. |
On-call Engineer, Subject Matter Expert |
|
Communications Manager |
Manages internal and external communications during an incident. |
Collects feedback and liaises with executives. |
Communications Officer |
|
Customer Support Lead |
Ensures timely responses to customer inquiries during an incident. |
Passes on relevant customer details to the incident team. |
Help Desk Lead |
|
Subject Matter Expert |
Offers specialized technical knowledge to address the incident. |
Provides context and alerts additional experts as needed. |
Technical Lead |
|
Social Media Lead |
Communicates updates on social channels in real time. |
Updates status pages and relays customer feedback. |
Social Media Manager |
|
Scribe |
Records key details and maintains an incident timeline. |
Keeps a record of activities and decisions. |
– |
|
Problem Manager |
Investigate root causes and recommend improvements post-incident. |
Coordinates postmortems and tracks remediation efforts. |
Root Cause Analyst |
Key Components Of An Effective Cyber Incident Response Plan
Impact assessment
When an incident occurs, the first task is to assess its impact. You need to determine which systems have been affected and what data might be at risk.
It helps understand how the incident affects your business, from customer trust to supply chain operations.
Monitoring, detection, and reporting
Effective cyber incident response depends on early detection. Use advanced tools to monitor your systems in real time to spot anomalies quickly.
Once you detect an incident, have a clear reporting protocol so everyone knows about it and can start working together to contain the threat.
Response, containment, and recovery
With the incident identified, the next step is to contain it. Isolate the affected systems and stop further damage. Then, focus on recovery: restore systems from backups, apply necessary patches, and update security measures.
Post-incident review and improvement
After the dust settles, it’s time to review what happened. Gather your team for a debrief to discuss what worked and what didn’t.
This learning phase is crucial. It helps refine your plan and ensures you’re even better prepared for future incidents.
Steps Involved In Cyber Incident Response Process
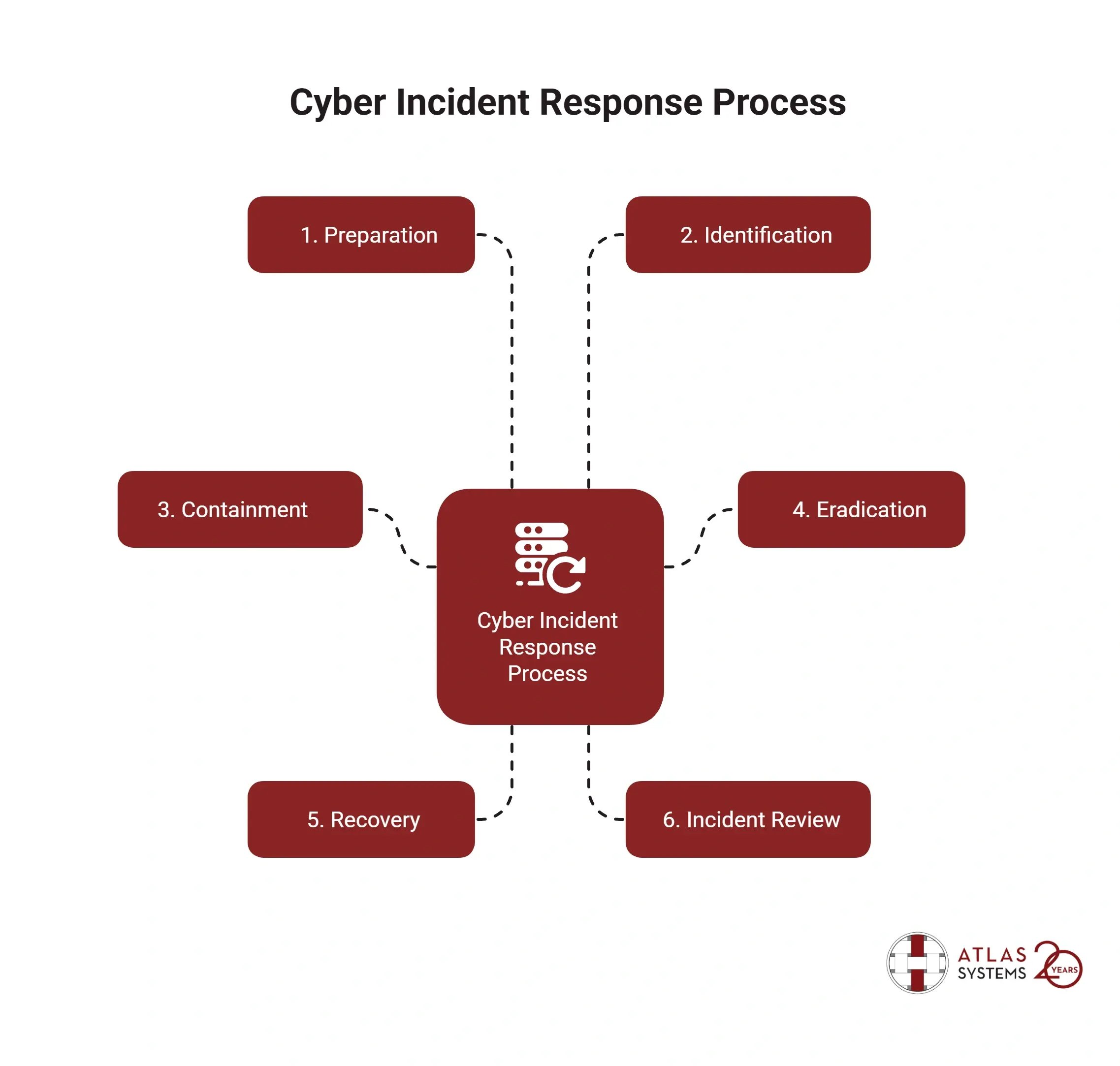
1. Preparation
Your cyber incident response team must be ready to act when a cyberattack hits. Preparation is all about laying the groundwork so everyone knows exactly what to do when the time comes. Here’s how you can get your team ready:
- Define clear roles: Make sure every team member knows their responsibilities–handling technical fixes, managing communications, or documenting the incident
- Set communication protocols: Establish step-by-step internal and external communication procedures so the right people get the information immediately
- Document the process: Create guidelines for recording every step of the incident response to navigate the crisis and provide valuable insights for future improvements
2. Identification
Now that your team is ready, it's time to figure out what kind of incident you're dealing with. Cyber threats constantly evolve, but most incidents can be grouped into a few common types. Here’s how you can approach it:
- Monitor and gather evidence: Keep a close eye on your systems and use threat intelligence tools to catch unusual activity
- Analyze the data: Look at logs and alerts to understand the nature and scope of the incident
- Categorize the incident: Most incidents fall into categories like:
- Ransomware
- Phishing
- DDoS attacks
- Malware infections
- Insider threats
- Social engineering
3. Containment
Once you've identified an incident, the next step is to contain it. This stops the threat from spreading and minimizes the damage.
Essentially, containment is your immediate response to ensure the issue doesn't escalate further. Here are some practical steps and common containment strategies:
- Isolate affected systems: Quickly disconnect compromised devices from the network to prevent the threat from moving laterally
- Restrict access: Limit user permissions and block suspicious activities to reduce further exposure
- Monitor and analyze: Keep a close watch on network traffic and logs to ensure the containment measures are effective and to detect any ongoing issues
Common containment strategies:
- Network segmentation: Divide your network into smaller, isolated zones so that a breach in one area doesn't affect the entire system
- Firewall and access control adjustments: Update firewall rules and tighten access controls to block malicious traffic
- Endpoint isolation: Remove or quarantine infected devices to stop the spread of malware
- Traffic filtering: Use intrusion prevention systems (IPS) to filter unwanted or suspicious traffic
- Temporary shutdown: In extreme cases, shut down certain systems or services to halt the attack while you work on a permanent solution
4. Eradication
Eradicating a cyber threat involves removing every last trace of the intrusion and understanding exactly how it happened so that you can prevent it in the future.
Once you've contained the incident, your team focuses on pinpointing the point of intrusion, assessing the entire attack surface, and closing any backdoor access that hackers might have left behind.
This step is critical because it stops the current threat and builds your defenses for what’s next.
Here’s how to approach eradication:
- Identify the intrusion point: Determine exactly where the attacker got in
- Assess the attack surface: Review all vulnerable areas to ensure no entry points remain
- Remove backdoor access: Eliminate any unauthorized access methods that could allow re-entry
- Neutralize remaining threats: Use tools like antivirus and anti-malware to clear the threat fully
- Determine the root cause: Analyze what led to the breach so you can update your security measures and prevent a similar attack
5. Recovery
After neutralizing the threat, recovery returns your systems to normal. At this point, incident responders work to completely eradicate any traces of malware, rebuild or restore systems from backups, and apply necessary patches so everything runs smoothly again.
How to implement recovery:
- Clean the systems: Eradicate any malware or unauthorized access
- Restore data: Rebuild your systems from verified, clean backups
- Patch and update: Apply all security patches to prevent similar issues
- Verify functionality: Test the systems to ensure they’re fully operational and secure
6. Incident Review
Once you're in the recovery process, it’s time to take a step back and review what happened. The goal is to learn from the incident, improve your defenses, and refine your response plan for the future.
How to implement incident review:
- Analyze the incident: Identify what led to the breach and what worked well in your response
- Document lessons learned: Record what could be improved, including processes, tools, and training
- Update your plan: Adjust your security measures and cyber incident response protocols based on the insights gained
- Share findings: Communicate the review outcomes with key stakeholders to foster a culture of continuous improvement
Cyber Incident Response Frameworks
The top incident response frameworks recommended by experts are:
- NIST SP 800-61 (Computer Security Incident Handling Guide): A comprehensive guide outlining best practices for detecting, responding to, and recovering cybersecurity incidents
- SANS Institute Incident Response Process: Known for its practical, step-by-step approach, many organizations have successfully adopted this process to streamline their response efforts
- ISO/IEC 27035: Provides a structured approach for incident management and response as part of an overall information security management system.
- CERT/CC Guidelines: Developed by the Computer Emergency Response Team Coordination Center experts, these guidelines focus on fostering strong collaboration and clear communication during incidents
Best Practices Of Cyber Incident Response
Here are some best practices of cyber incident response you should know:
 Holistic Alerting
Holistic Alerting
You know the saying, “Who’s guarding the guards?” Well, it applies here too. It’s essential to ensure that the tools monitoring your systems are being watched. Regular checks on your alerting systems help you catch any failures before they become bigger issues.
Learn from Every Incident
It’s common for IT and DevOps teams to focus only on major outages, but even smaller incidents can offer valuable insights. Don’t overlook them—taking time for a quick postmortem can help you identify gaps and improve your overall response strategy.
Effective Employee Onboarding and Training
Bringing new team members up to speed should happen early, not during a crisis. Ensure everyone on your incident response team is well-trained and understands their role. This way, long-time staff or new hires filling gaps can hit the ground running when an incident occurs.
Continuous Systems Testing
Regular defense testing should be part of your everyday operations. Testing during the preparation and threat identification phases helps uncover vulnerabilities before an attack occurs, ensuring your systems and monitoring tools are always ready.
How Can Atlas Systems Help?
A solid incident response plan is your safety net. It helps you recover from cyber incidents and reinforces your overall cybersecurity posture. When an incident occurs, you need to know who’s responsible, how to contain the threat, and most importantly, how to restore normal operations with minimal disruption.
That’s where Atlas Systems comes in.
Atlas Systems offers an end-to-end cybersecurity solutions suite to keep your business secure and resilient. Here’s how we help:
- 24/7 Managed Detection and Response (MDR Solutions): Our team continuously monitors your systems for unusual activities using advanced AI-based threat intelligence
- Threat and Vulnerability Management: We conduct regular vulnerability scans and risk assessments to identify and address weak points before they can be exploited
- Cloud and API Security: Our solutions safeguard your digital assets by providing real-time monitoring and protection against data leaks and unauthorized access
If you’re ready to take your cybersecurity to the next level, schedule a consultation with us today, and let’s work together to safeguard your future.
FAQs Cyber Incident Response
How can organizations test the effectiveness of their incident response plans?
Organizations can regularly conduct simulated exercises and tabletop drills to identify gaps and refine their procedures, ensuring every team member is prepared. This hands-on testing helps validate the plan’s effectiveness in real-world scenarios.
What legal considerations should be taken into account during incident response?
Complying with data breach notification laws, preserving evidence for potential litigation, and consulting legal experts to wade through regulatory obligations are important. These steps help mitigate legal risks and ensure proper handling of sensitive information during an incident.
What are the benefits of involving third-party experts in incident response?
Third-party experts like Atlas Systems bring specialized knowledge, an unbiased view, and advanced capabilities to enhance your incident response. Our involvement often accelerates recovery, identifies hidden vulnerabilities, and helps ensure compliance with industry standards.
Reinventing TPRM with ComplyScore® Executive Guide
- Turn alerts into accountable actions
- Instant, explainable compliance powered by AI + HITL
- Achieve 90–95% vendor coverage in under 10 days
Related Reading
Blogs
.png?width=869&height=597&name=image%20(5).png)
-1.png?width=486&height=315&name=IDC%20Banner%20(1)-1.png)
.png?width=300&height=175&name=Rectangle%2034624433%20(2).png)













.png)
