Comprehensive Cybersecurity Risk Management for Complete Protection
Identify vulnerabilities, test defenses, and protect your digital assets with AI-based cybersecurity solutions that adapt to evolving threats.
24/7
Continuous monitoring
Real-Time
Threat detection
End-to-End
Protection across your cyber environment
Trusted partner to market-leading brands

Comprehensive scanning
Continuous assessment
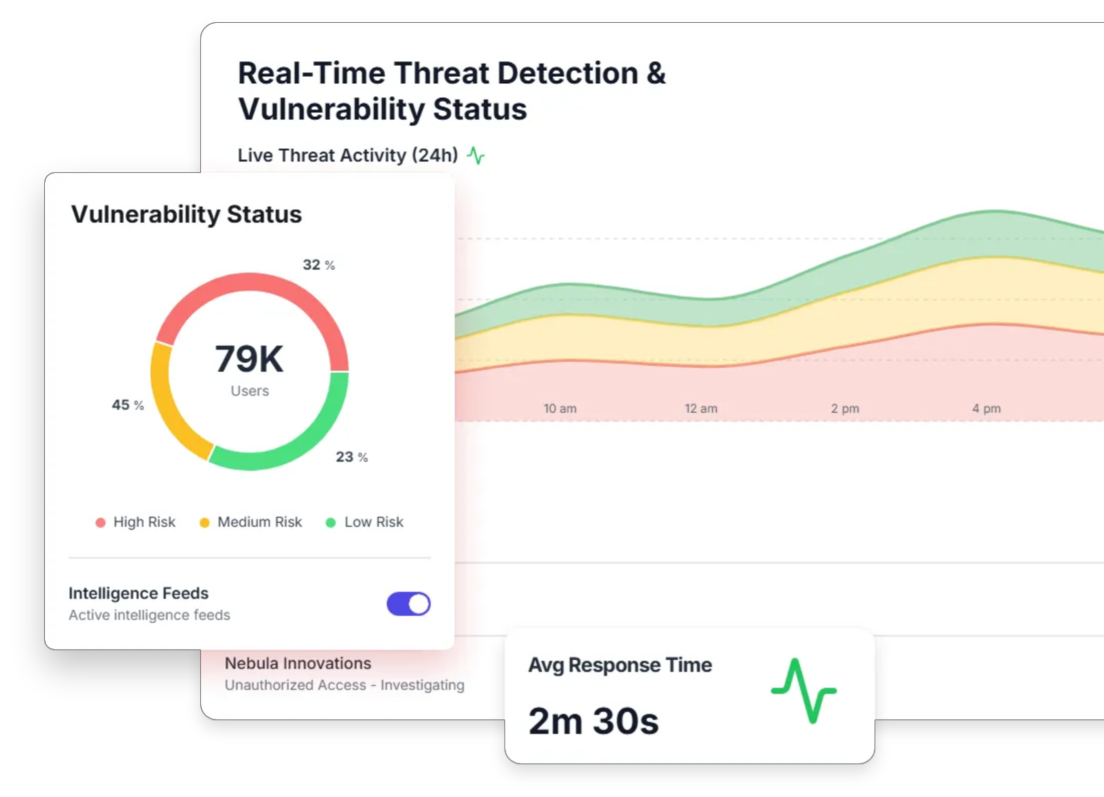
Identify Vulnerabilities Before Exploitation
Analyze security holes, outdated software, and misconfigured systems across your IT environment with comprehensive scans. Receive detailed reports describing vulnerabilities by identifying potential weaknesses. ComplyScore®’s continuous risk assessment prioritizes threats according to severity and provides actionable information for proactively addressing gaps.
Each vendor gets the right level of review under your policies and SLAs.

Simulated cyber attacks
Exploitable vulnerability insight
Test Defenses with Real-World Attacks
Penetration testing measures how well your defenses work by simulating real-world attacks that traditional scanning might miss. ComplyScore®’s security experts attempt to attack system vulnerabilities to identify weaknesses that hackers may target. You gain a thorough picture of all security holes in your system, enabling you to fortify defenses and stop potential assaults with intelligent, preventative measures.
You maintain strategic oversight while we deliver finished assessments in <10 days vs. the industry average of 30-45 days.

24/7 threat detection
Rapid incident response
Monitor and Respond in Real-Time
Managed Detection and Response services keep an eye on your systems and networks continuously to detect unusual activities and take appropriate action. Rapid incident response and threat containment minimize damage from security events. Expert threat analysis and response strategies ensure your organization maintains business continuity despite evolving cyber threats.
Your program stays current without manual checks or missed signals.

Cloud protection
Application security
Secure Critical Assets
Protect cloud environments and API endpoints from unauthorized access, data breaches, and cyber threats. Protect your software development lifecycle by finding code vulnerabilities and guarding against attacks like SQL injection and cross-site scripting. ComplyScore® ensures only authorized individuals access your systems and sensitive data through strong authentication, secure provisioning, and real-time access monitoring with anomaly detection.
Your team focuses on strategy while we coordinate execution.

Transform Your TPRM Program
Proven Results Across Industries
Trusted partner to market-leading brands
Atlas far exceeds our requirements...
One of the key differentiators between Atlas and other governance, risk and compliance and 3rd party risk management tools is the ease of use of the Atlas solutions. Also from a total cost of ownership perspective, Atlas far exceeds those requirements in terms of being very cost efficient in delivering all this.
Izhar Mujaddidi,
Senior Director, Cybersecurity, Carelon Behavioral Health
ComplyScore is highly responsive and adaptable
ComplyScore is highly responsive and adaptable to our evolving processes and requirements, proving to be a trusted partner at every step. Their security analysts were knowledgeable, flexible, and delivered exceptional services that consistently exceeded our expectations.
Enterprise Client
G2 Review (Jan 2025)
My experience has been largely positive
I have been using ComplyScore for several months and my experience has been largely positive. The platform provides comprehensive solutions for compliance management and streamlines our operations efficiently.
Mid-Market Company,
Gartner Peer Insights (Sep 2024)
Trusted by Industry Leaders
Representative Vendor | Listed in 2025 Market Guide for TPRM Technology Solutions
Active partner member of the Third Party Risk Association
Trusted across healthcare, financial services, technology, and regulated industries
See ComplyScore® in Action
Book a 30-minute walkthrough showing how Atlas Systems' certified analysts will execute your assessments, monitor your vendors, and coordinate remediations on the ComplyScore® platform.
Quick Answers
What's the difference between vulnerability assessment and penetration testing?
Vulnerability assessment provides comprehensive scans that identify security holes, out-of-date software, and misconfigurations across your environment. Penetration testing goes further by simulating actual cyberattacks to exploit those vulnerabilities, showing you exactly how hackers could breach your defenses. Both services work together to give you complete visibility into your security posture.
How quickly can you detect and respond to threats?
Managed Detection and Response services monitor your systems 24/7 with continuous surveillance. Advanced analytics and threat intelligence identify unusual activities in real-time, enabling rapid incident response and threat containment before damage occurs. Expert analysis ensures appropriate response strategies based on threat severity and business impact.
What types of applications and cloud environments do you secure?
Application security covers your entire software development lifecycle, protecting web and mobile apps against threats like SQL injection and cross-site scripting. Cloud security protects your cloud infrastructure and API endpoints from unauthorized access and data breaches, with real-time monitoring of API usage patterns and protection against data leaks across all major cloud platforms.




















.png?width=387&height=387&name=image%20(5).png)